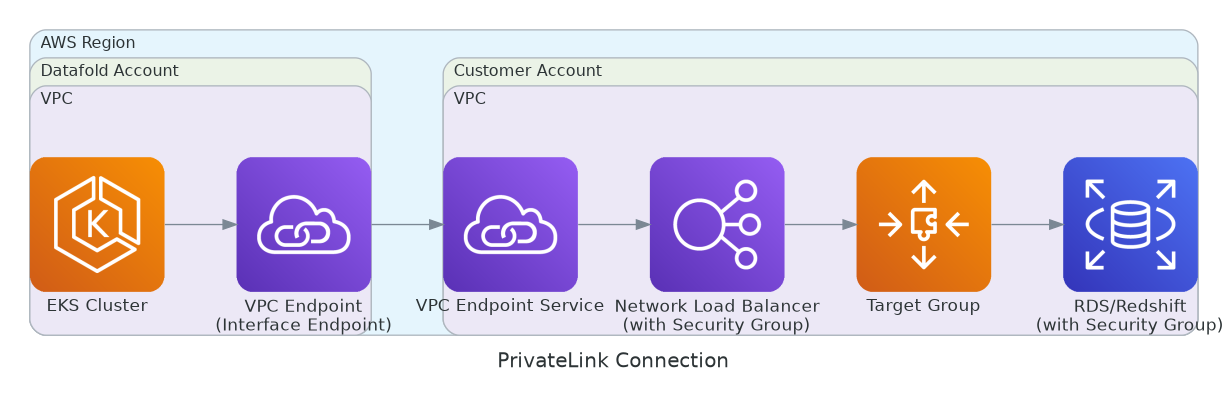
Overview
The setup involves creating a Network Load Balancer (NLB) and VPC Endpoint Service in your AWS account that Datafold can connect to via a VPC Endpoint.- Enhanced Security: Database traffic never traverses the public internet
- Reduced Attack Surface: No need to configure internet gateways or NAT gateways
- Simplified Network Architecture: No complex VPN or firewall rules
- Scalability: Support for multiple databases across multiple regions
For HA setups with Primary and Read Replica, the NLB should target both instances.
Prerequisites
- RDS, Aurora, Redshift, or other database instance in AWS
- IAM permissions for creating NLBs, VPC Endpoint Services, security groups, and target groups
- Contact Datafold Support (support@datafold.com) to receive the Role ARN for the PrivateLink connection
Setup Process
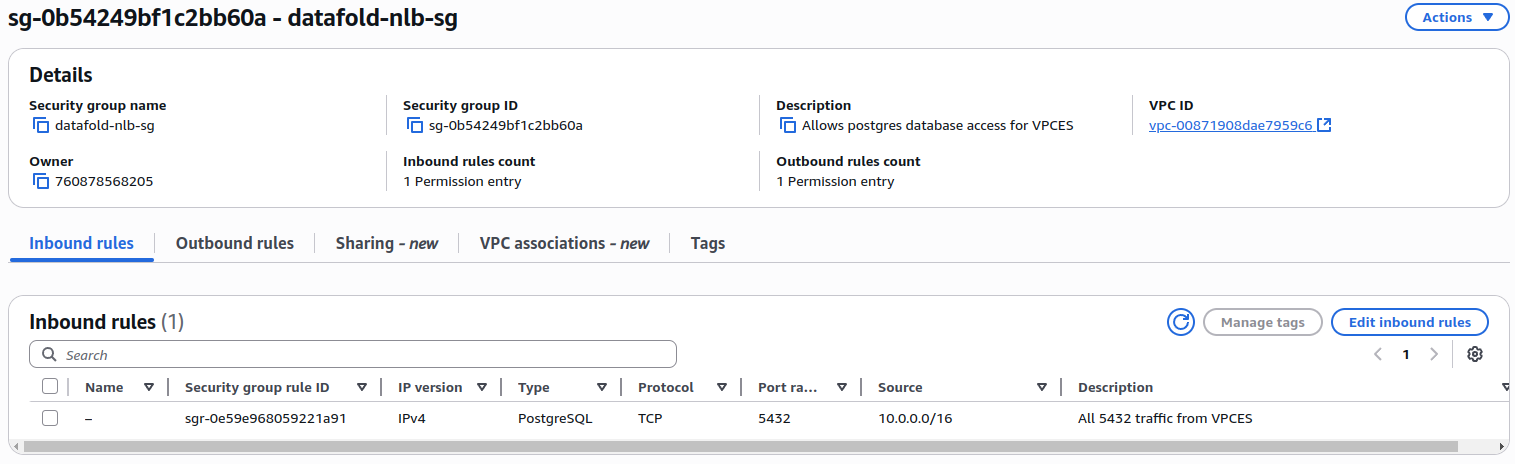
The components must be configured in this specific order, working from your data source backwards to the VPC Endpoint Service. This is because resources that you create in each step are used by resources that come before it.Step 1: Create NLB Security Group
Create a security group for the Network Load Balancer:- Navigate to VPC > Security Groups and click Create security group
- Configure:
- Name: e.g.,
datafold-nlb-sg - VPC: Same VPC as your database
- Name: e.g.,
- Add inbound rule:
- Type: Custom TCP
- Port: Your database port
- Source: The CIDR blocks of the VPC you’re installing the NLB in.
- Add outbound rule:
- Type: Custom TCP
- Port: Your database port
- Destination: The security group of your database
Step 2: Verify Data Source Security Group
Check the security group attached to your database (RDS, Redshift, etc.) and ensure it allows inbound traffic on the database port from the NLB security group (which you created in Step 1). You can either use the ID of the NLB security group or use another appropriate CIDR range or security group id.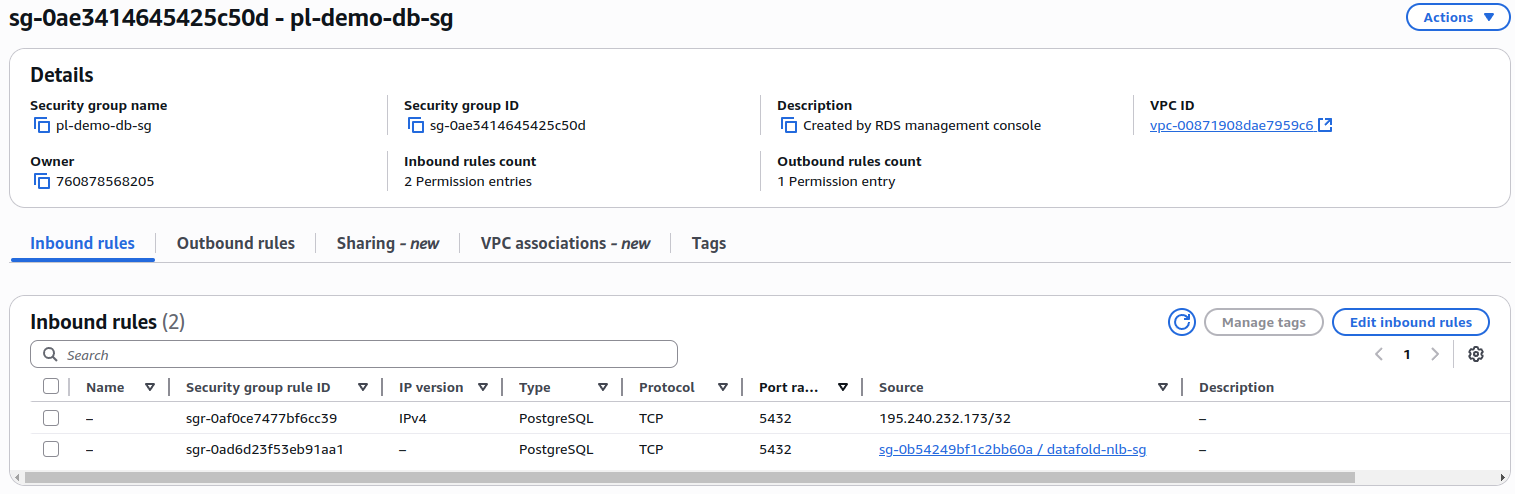
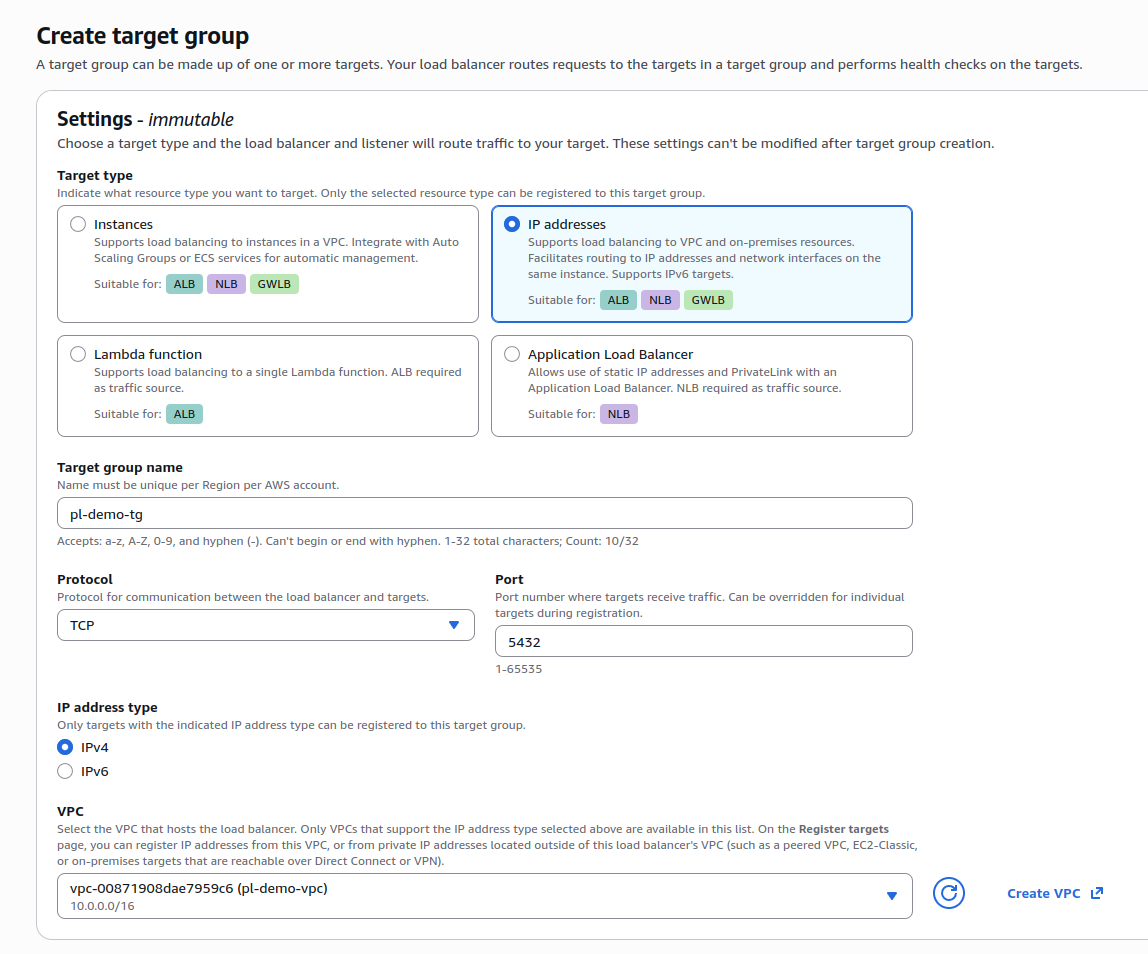
Step 3: Create Target Group
Create a target group that points to your database:- Navigate to EC2 > Target Groups and click Create target group
- Configure the target group:
- Target type: IP addresses (for RDS/Aurora) or Instances
- Protocol: TCP
- Port: Your database port (e.g., 5432 for PostgreSQL, 3306 for MySQL)
- VPC: Select the VPC where your database resides
- Configure health checks with appropriate settings:
- Protocol: TCP
- Port: Same as your database port
- Register your database as a target using its private IP address
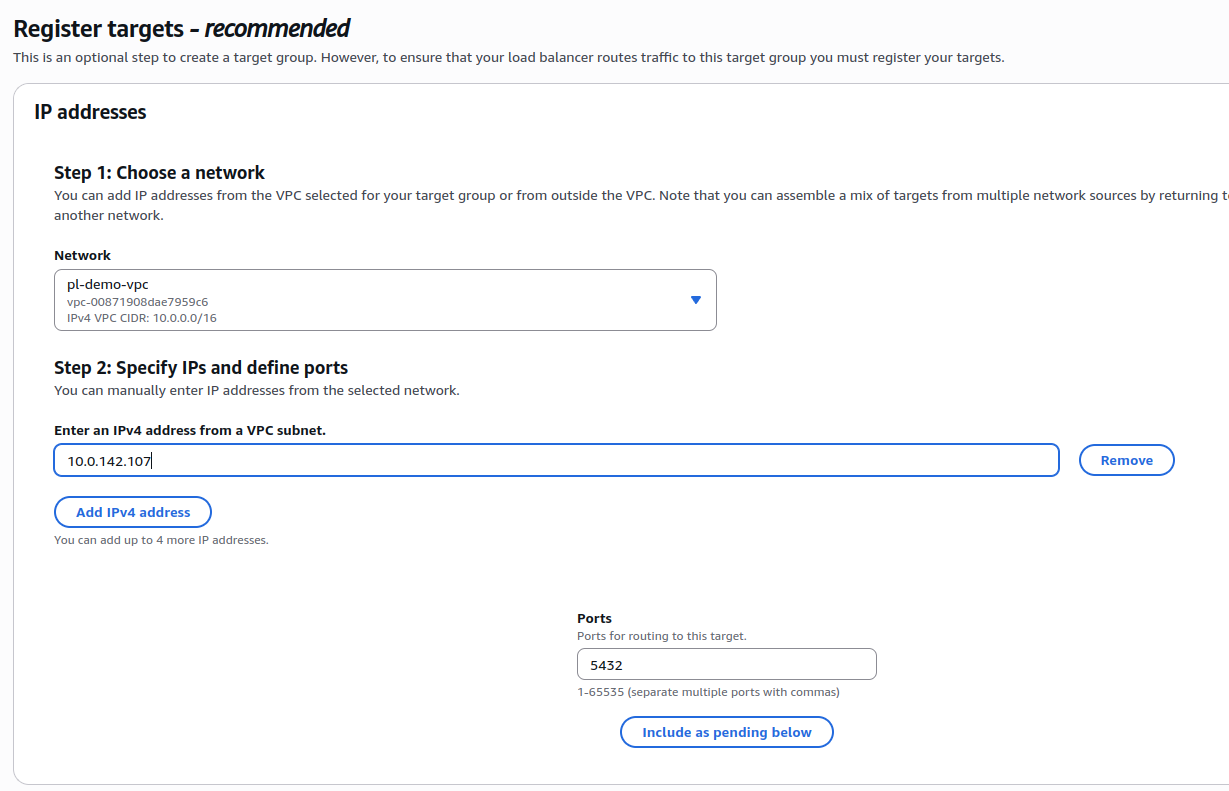
- The target group will not yet show healthy status for the targeted database because the NLB is not set up yet. The health status details will say: “Target group is not configured to receive traffic from the load balancer”.
Step 4: Create Network Load Balancer
Create the NLB that will route traffic to your database:- Navigate to EC2 > Load Balancers and click Create Load Balancer
- Select Network Load Balancer
- Configure:
- Name: e.g.,
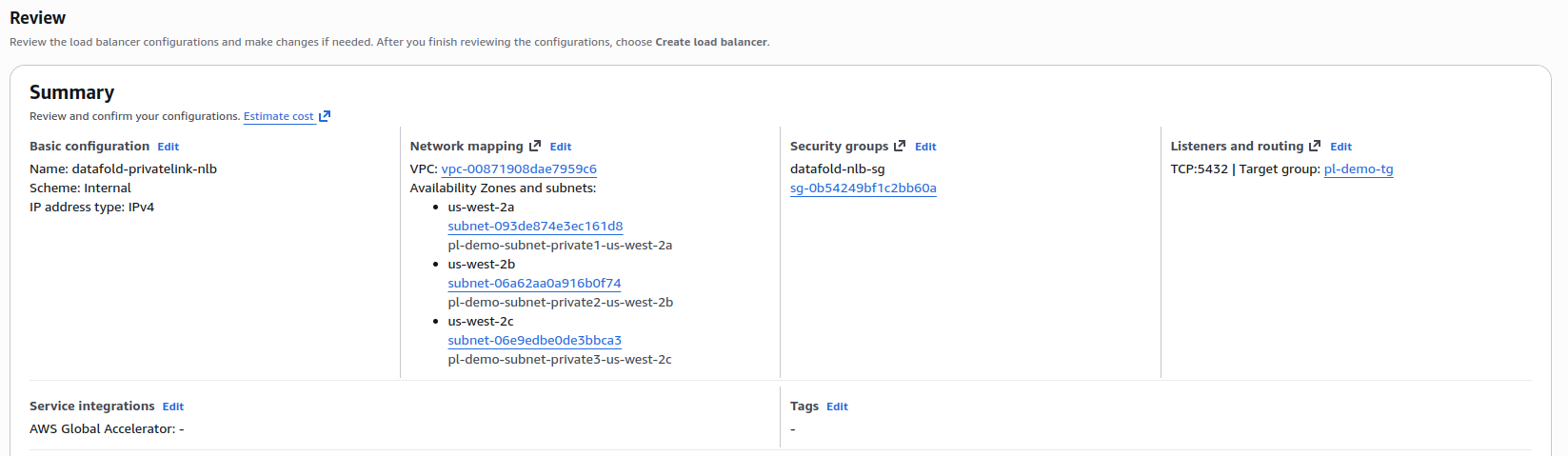
datafold-privatelink-nlb - Scheme: Internal
- IP address type: IPv4
- VPC: Same VPC as your database, or another VPC that your organization has deemed appropriate.
- Mappings: Select availability zones where you want to route traffic from and select the correct subnet for each availability zone.
- Security groups: Attach the security group created in Step 1
- Name: e.g.,
- Configure listener:
- Protocol: TCP
- Port: Your database port (e.g., 5432, 3306, 5439)
- Default action: Forward to the target group created in Step 3
- Create the load balancer and wait for it to become active
Step 5: Create VPC Endpoint Service
Create the VPC Endpoint Service that exposes your NLB to another account over the AWS networking infrastructure:- Wait for the NLB created in the previous step to fully provision. It should show Active when the NLB is fully provisioned.
- Navigate to VPC > Endpoint Services and click Create endpoint service
- Configure:
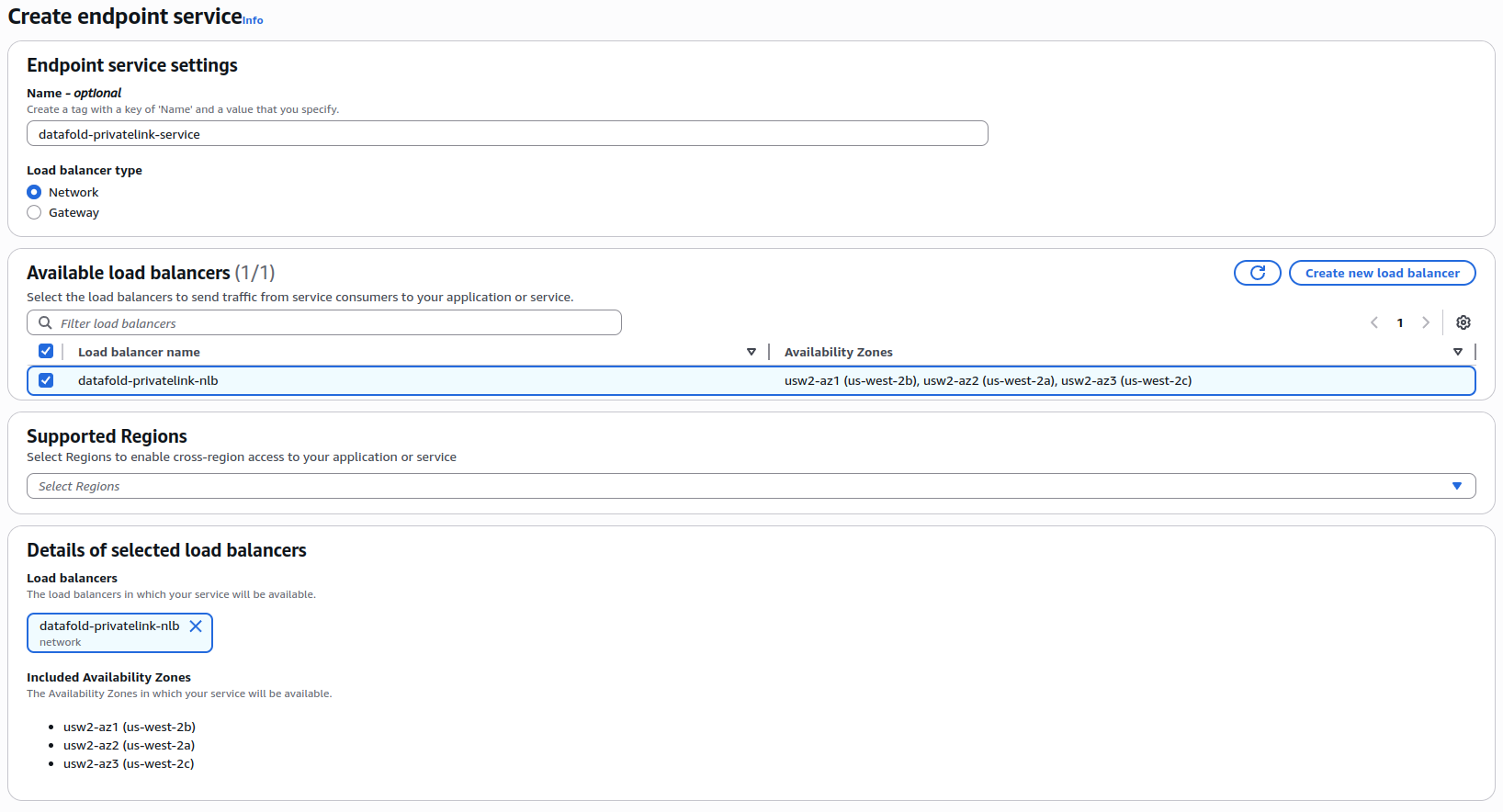
- Name: e.g.,
datafold-privatelink-service - Load balancer type: Network
- Available load balancers: Select the NLB created in Step 4
- Require acceptance: Enable this option if you want to individually accept every endpoint attempting to connect.
- Supported availability zones: Select the same AZ coverage as your NLB.
- Name: e.g.,
- Create the endpoint service
- Once created, note the Service name (format:
com.amazonaws.vpce.<region>.vpce-svc-xxxxxxxxx) - Add allowed principal. This step is necessary so that Datafold can see this VPC Endpoint Service. It will be invisible otherwise:
- Click on the endpoint service
- Go to Allow principals tab
- Click Allow principals
- Enter the Role ARN provided by Datafold Support
- Click Allow principals
- Note the Availability Zone IDs from the Details tab. These are the zone id’s, not zone names, characterized by
usw2-az3or similar names.
Step 6: Send Information to Datafold
Provide the following information to Datafold Support:- VPC Endpoint Service name (from Step 5)
- Availability Zone IDs (from Step 5)
- Database port that the NLB is listening on
- AWS region where the service is located
Step 7: Validate Configuration
To determine if the setup is complete and working, perform the following validation steps: 1. Verify Target Group Health Status- Navigate to EC2 > Target Groups
- Select the target group created in Step 3
- Go to the Targets tab
- Verify that your database target shows a Health status of “Healthy”
- If the status shows “Unhealthy”, check the health check configuration and ensure the security groups allow traffic between the NLB and database
- Check 1: Verify NLB to Database connectivity
- Check 2: Verify VPC Endpoint Service to NLB connectivity
- Target group shows “Healthy” status
- Both Network Reachability Analyzer checks are “Reachable”
Troubleshooting
Health checks failing on target group:- Verify the target IP address is correct
- Check that the database security group allows traffic from the NLB security group
- Ensure the database is running and accepting connections
- Verify the allowed principal (Role ARN) is correct
- Check that you accepted the endpoint connection request
- Ensure the Availability Zone IDs match between the endpoint service and endpoint
- Datafold has already verified connectivity from their saas cluster to their registered endpoint before reporting this failure
- Verify all security group rules are configured correctly on the NLB and the targeted database
- Check that the NLB listener is on the correct port
- Ensure the target group health checks are passing
Verifying Configuration with Network Reachability Analyzer
You can use AWS VPC Network Reachability Analyzer to verify that traffic can flow correctly through your PrivateLink setup. This is helpful for identifying security group or network ACL issues. Check 1: Verify NLB to Database connectivity- Navigate to VPC > Reachability Analyzer and click Create and analyze path
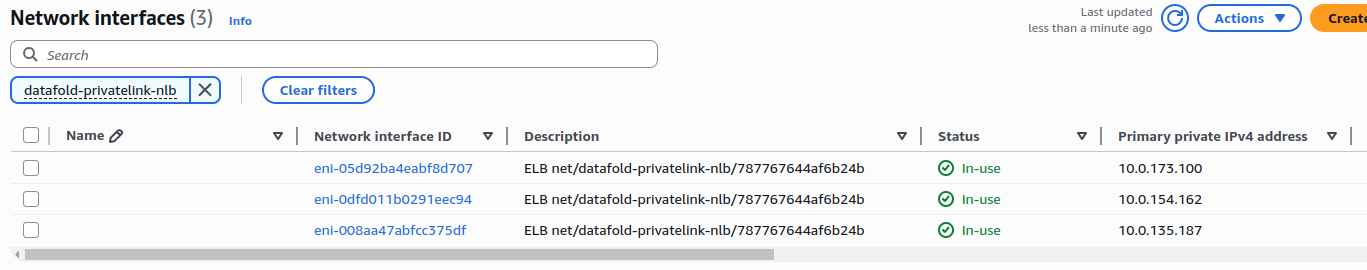
- Find the NLB network interface:
- Go to EC2 > Network Interfaces
- Search for your NLB name (e.g.,
datafold-privatelink-nlb) - Note one of the network interface IDs
- Record one of the NLB IPs for another test
- Configure the path:
- Source type: Network Interfaces
- Source: Select the NLB network interface
- Destination type: IP addresses
- Destination: Enter the private IP address of your database (RDS/Redshift endpoint)
- Destination port: Your database port (e.g., 5432, 3306, 5439)
- Protocol: TCP
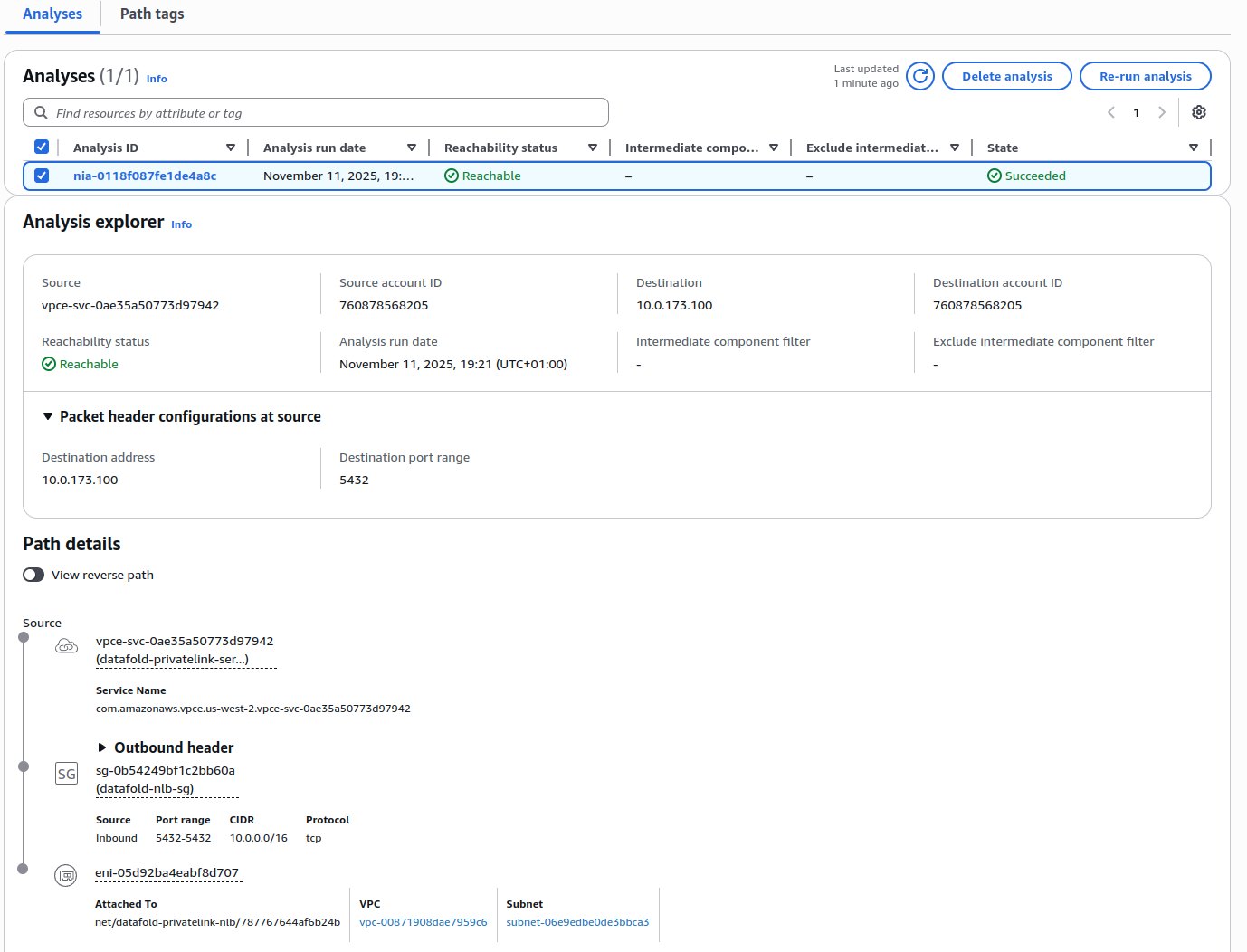
- Click Create and analyze path
- Review the results:
- Reachable: Traffic can flow from NLB to database ✓
- Not reachable: Check security groups and network ACLs blocking the path
- Create another reachability analysis:
- Source type: VPC Endpoint Services
- Source: Select your VPC Endpoint Service
- Destination type: Network Interfaces (or IP addresses)
- Destination: Select the NLB network interface or enter its IP address
- Destination port: Your database port
- Protocol: TCP
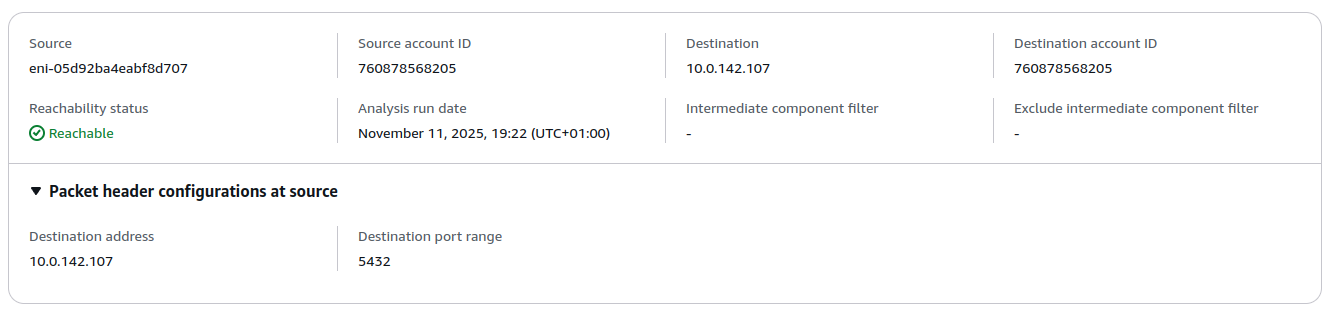
- Click Create and analyze path
- Review the results to ensure traffic can flow from the VPC Endpoint Service to the NLB across security groups, NACL rules and any other networking infrastructure you have inbetween.
