This feature is currently supported for Databricks, Snowflake, Redshift, and BigQuery.
Overview
The diagram below illustrates how the authentication flow proceeds:- Users authenticate using the configured OAuth provider.
- Users can then create diffs between data sets that their user can access using OAuth database permissions.
- During Continuous Integration (CI), Datafold executes diffs using a Service Account with the least privileges, thus masking sensitive/PII data.
- If a user needs to see sensitive/PII data from a CI diff, and they have permission via OAuth to do so, they can rerun the diff, and then Datafold will authenticate the user using OAuth database permissions. Then, the user will have access to the data based on these permissions.
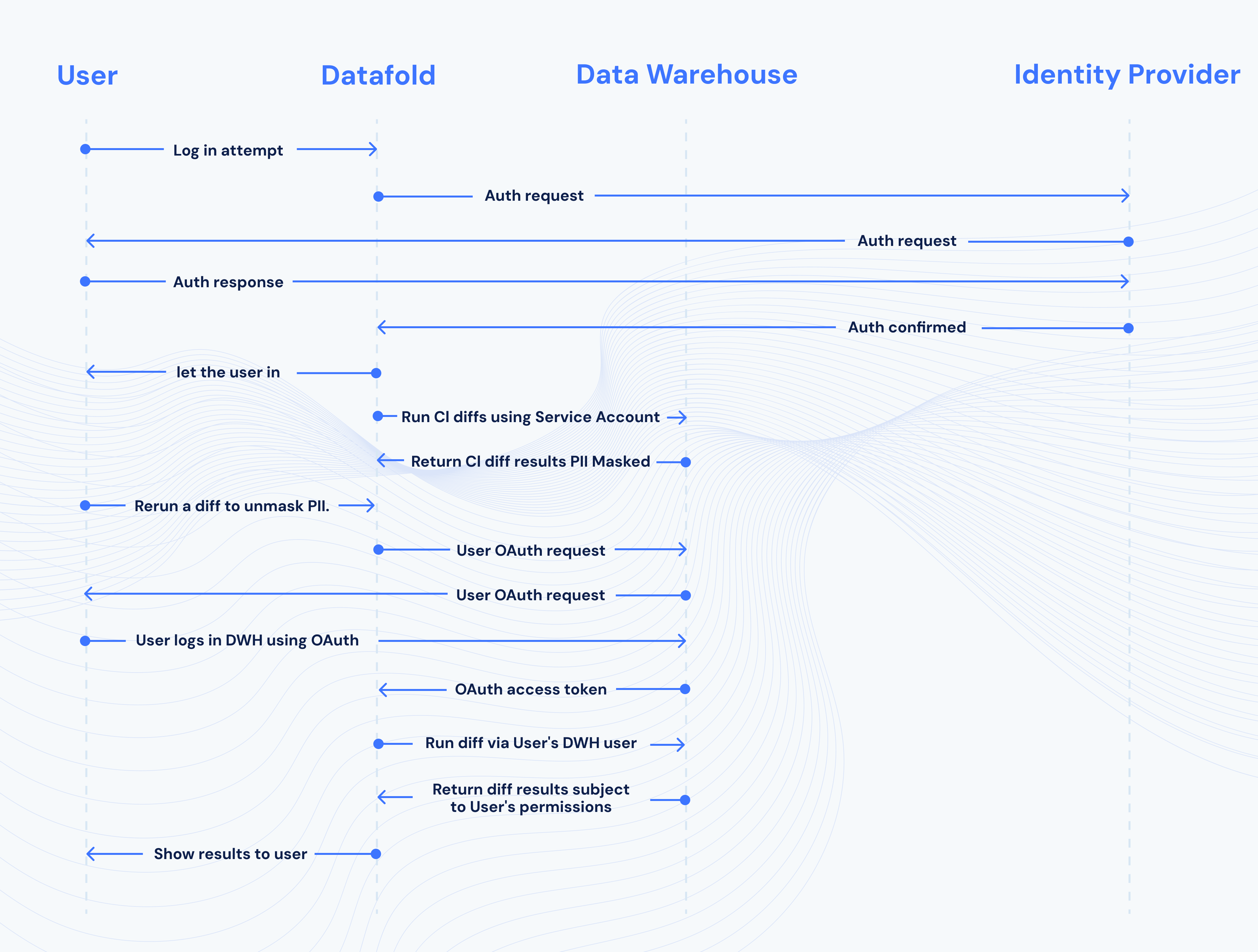
How it works
1. Create a Data Diff
When you attempt to run a data diff, you will notice that it won’t run without authentication: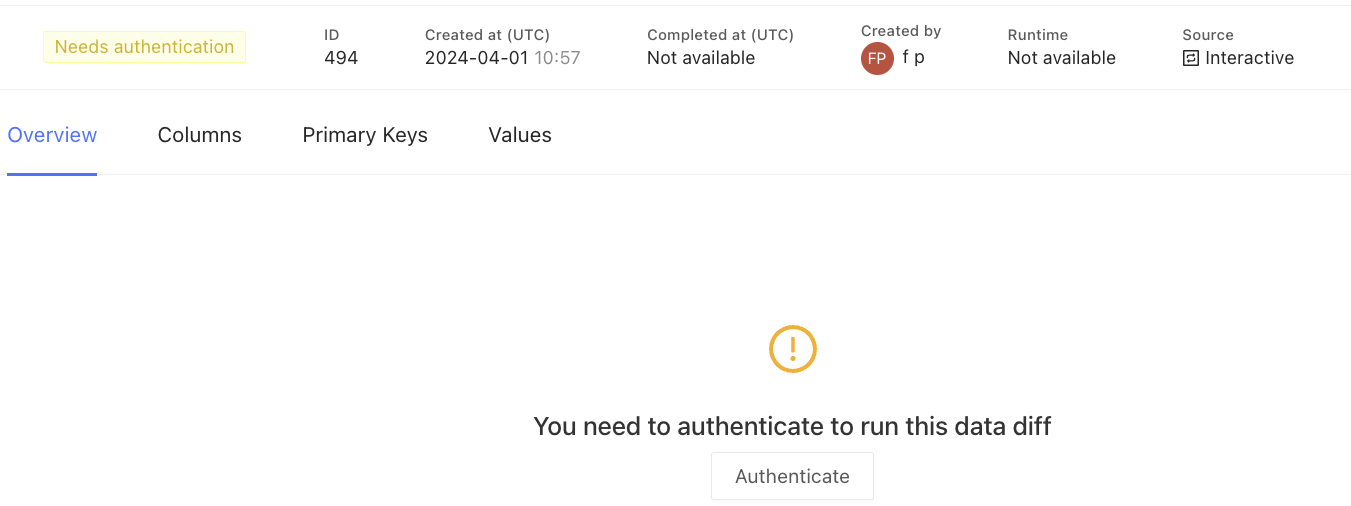
2. Authorize the Data Diff
Authorize the data diff by clicking the Authenticate button. This will redirect you to the data warehouse for authentication: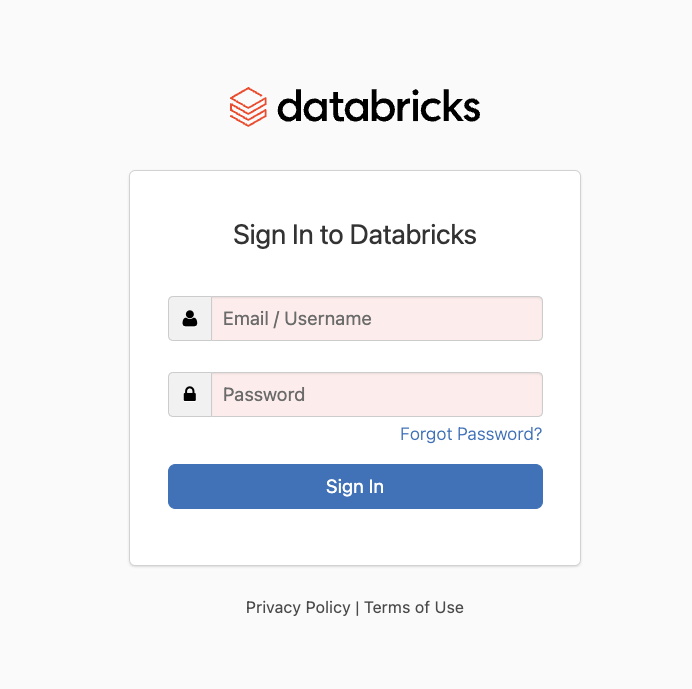
3. The Data Diff is now running
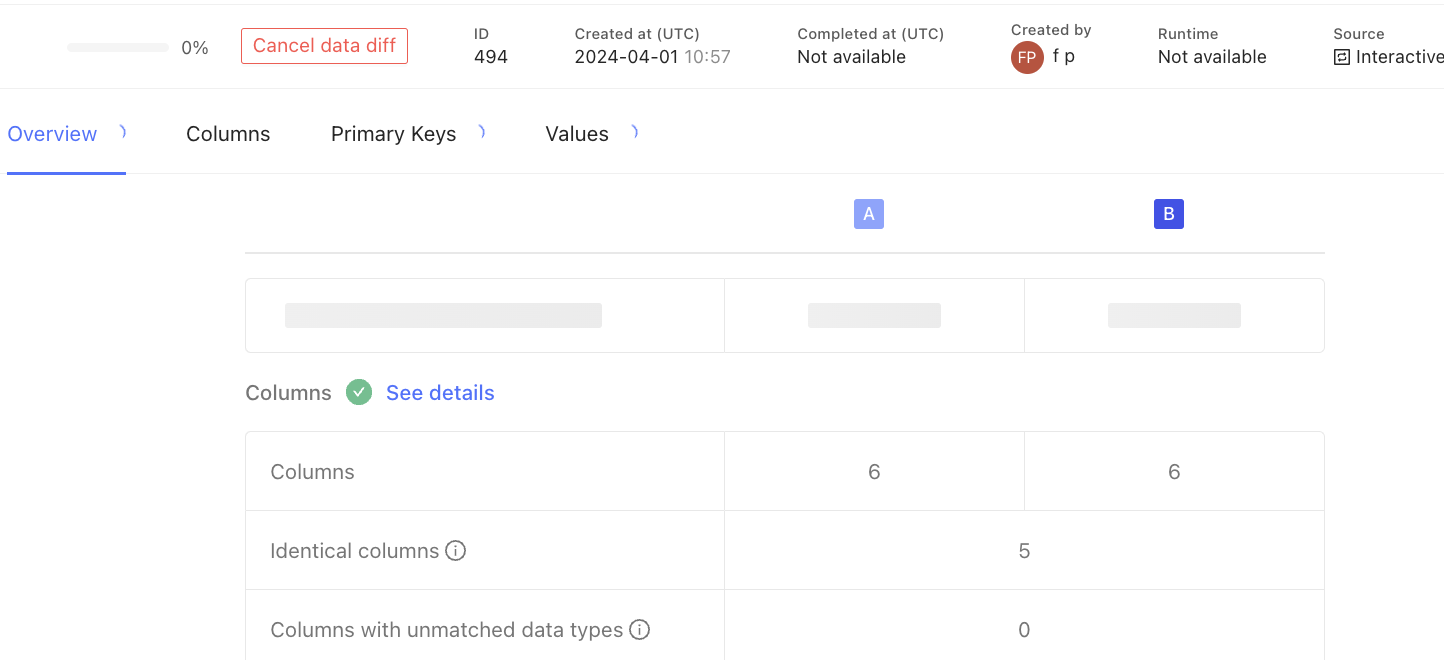
4. View the Data Diff results
The results reflect your permissions within the data warehouse: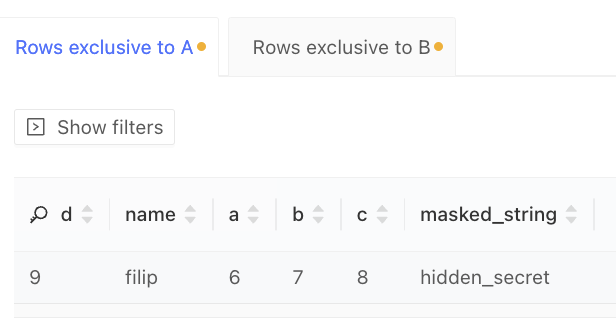
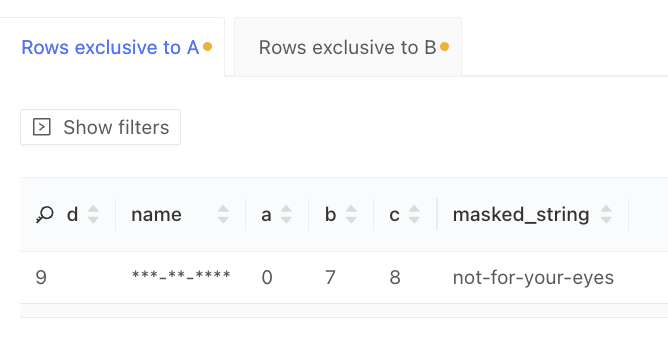
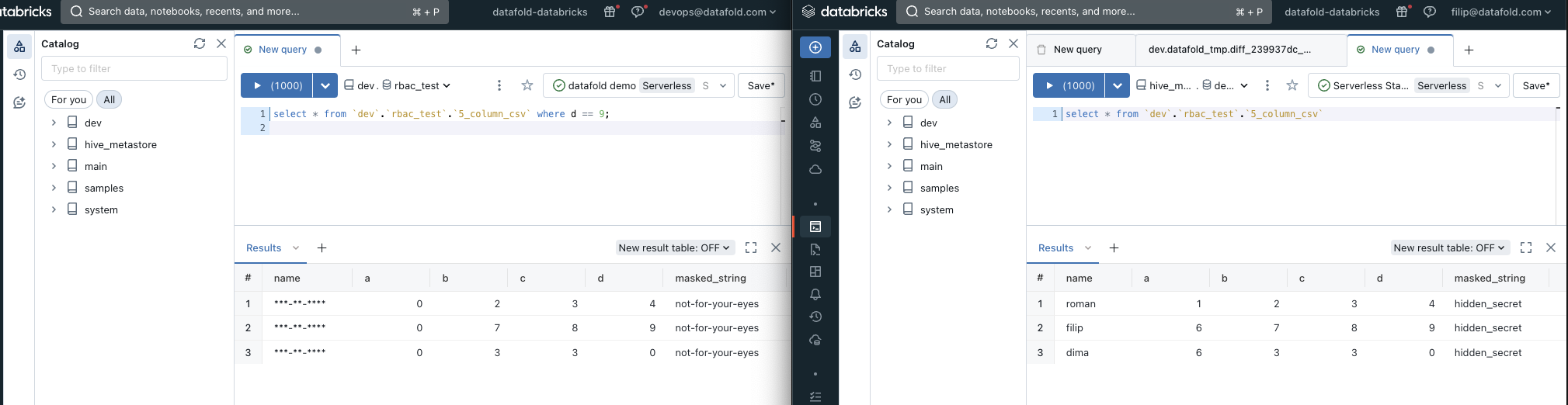
5. Sharing Data Diffs
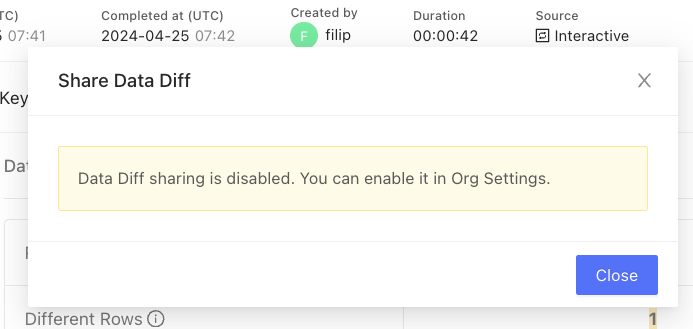
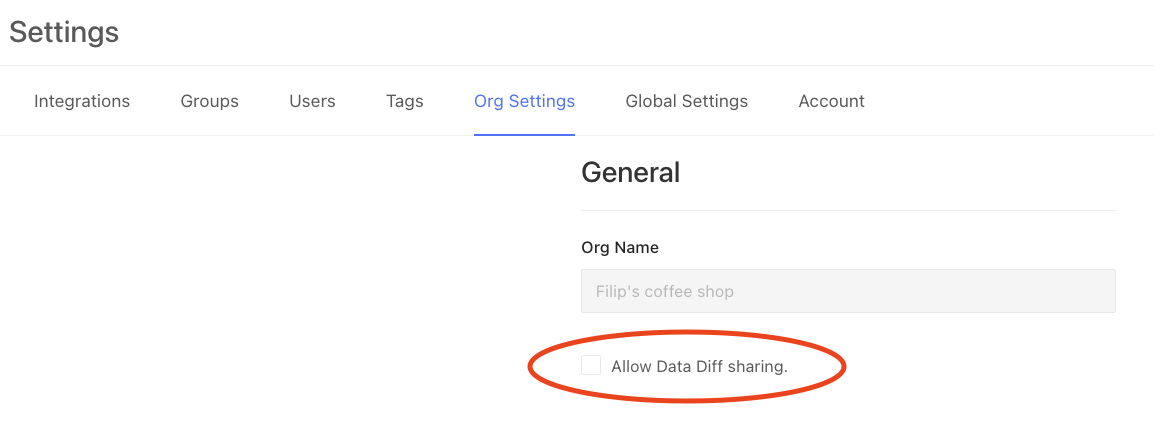
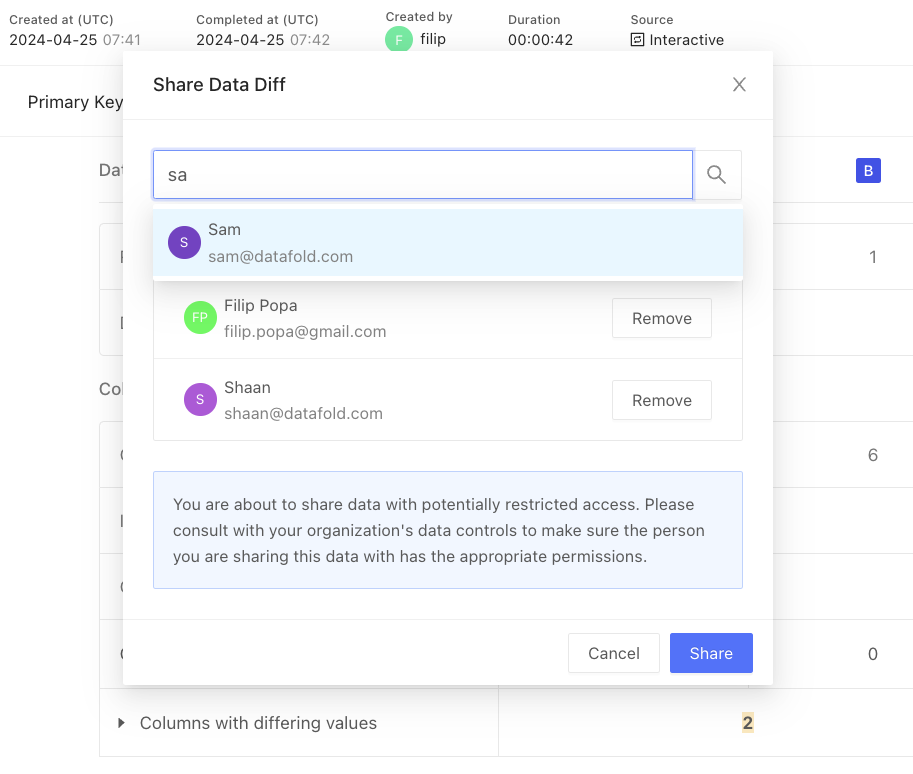
Data diff sharing is a feature that enables you to share data diffs with other users. This is useful in scenarios such as compliance verification, where auditors can access specific data diffs without first requiring permissions to be set up in the data warehouse. Sharing can be accessed via the Actions dropdown on the data diff page: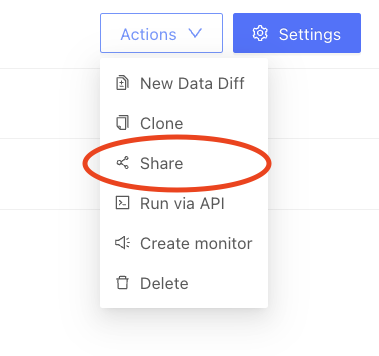
Configuring OAuth
Navigate to Settings and click on your data connection. Then, click on Advanced settings and under OAuth, set the Client Id and Client Secret fields: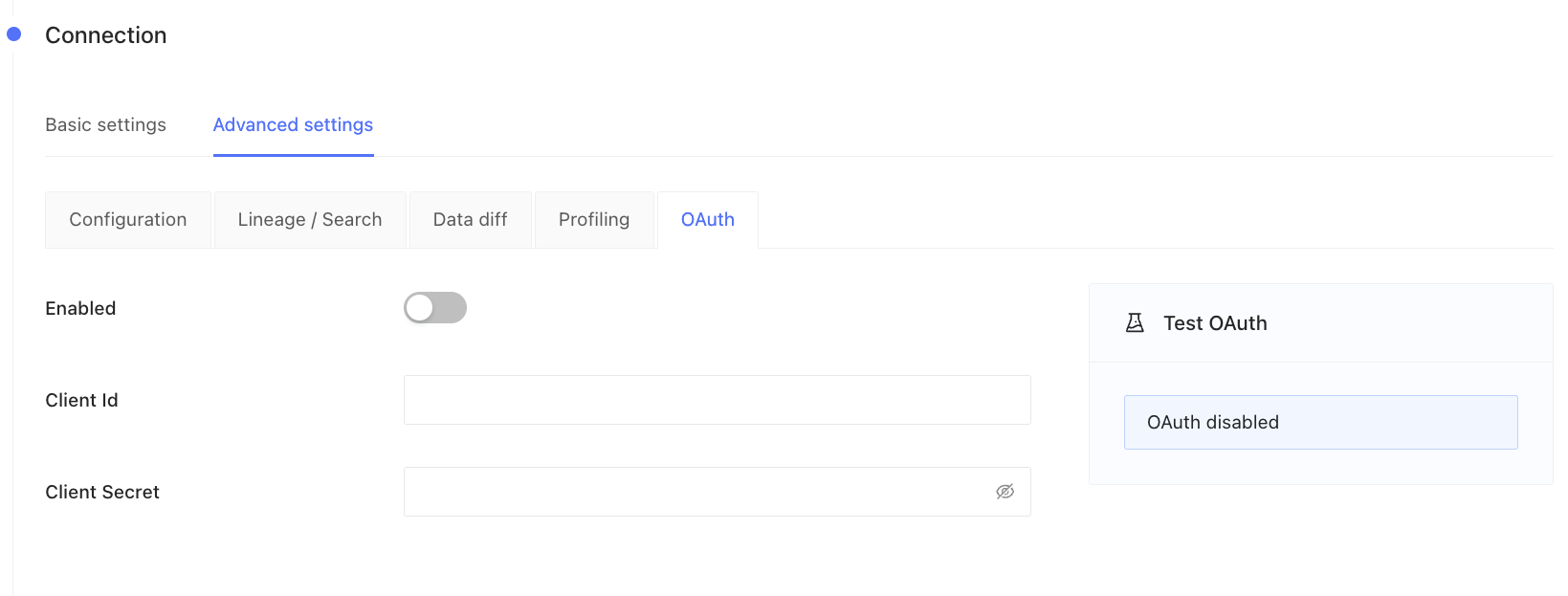
Example: Databricks
To create a new Databricks app connection:- Go to Settings and App connections.
- Click Add connection in the top right of the screen.
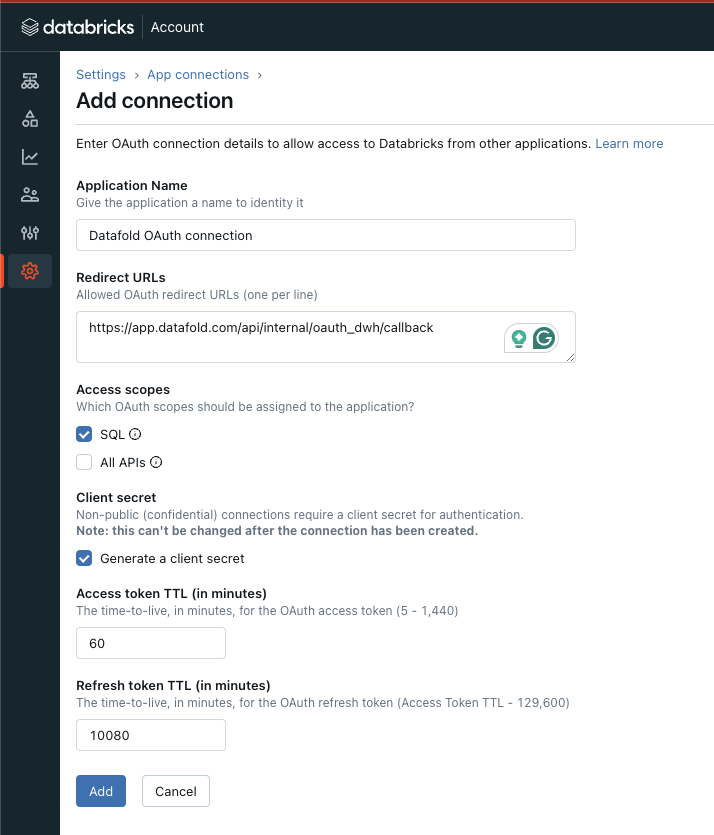
- Fill in the required fields:
Datafold caches access tokens and uses refresh tokens to fetch new valid tokens in order to complete the diffs and reduce the number of times users need to authenticate against the data warehouses.One hour is sufficient for the access token.The refresh token will determine the frequency of user reauthentication, whether it’s daily, weekly, or monthly.
- Click Add to obtain the Client ID and Client Secret.
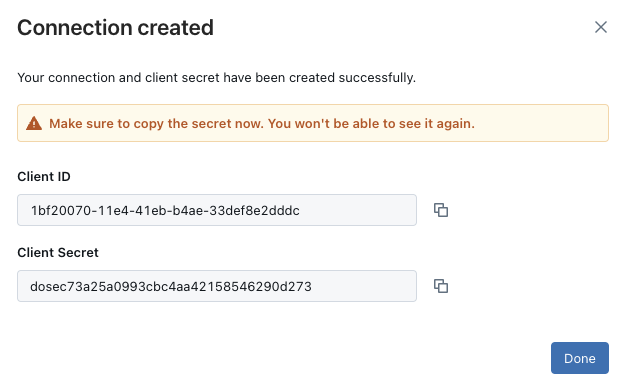
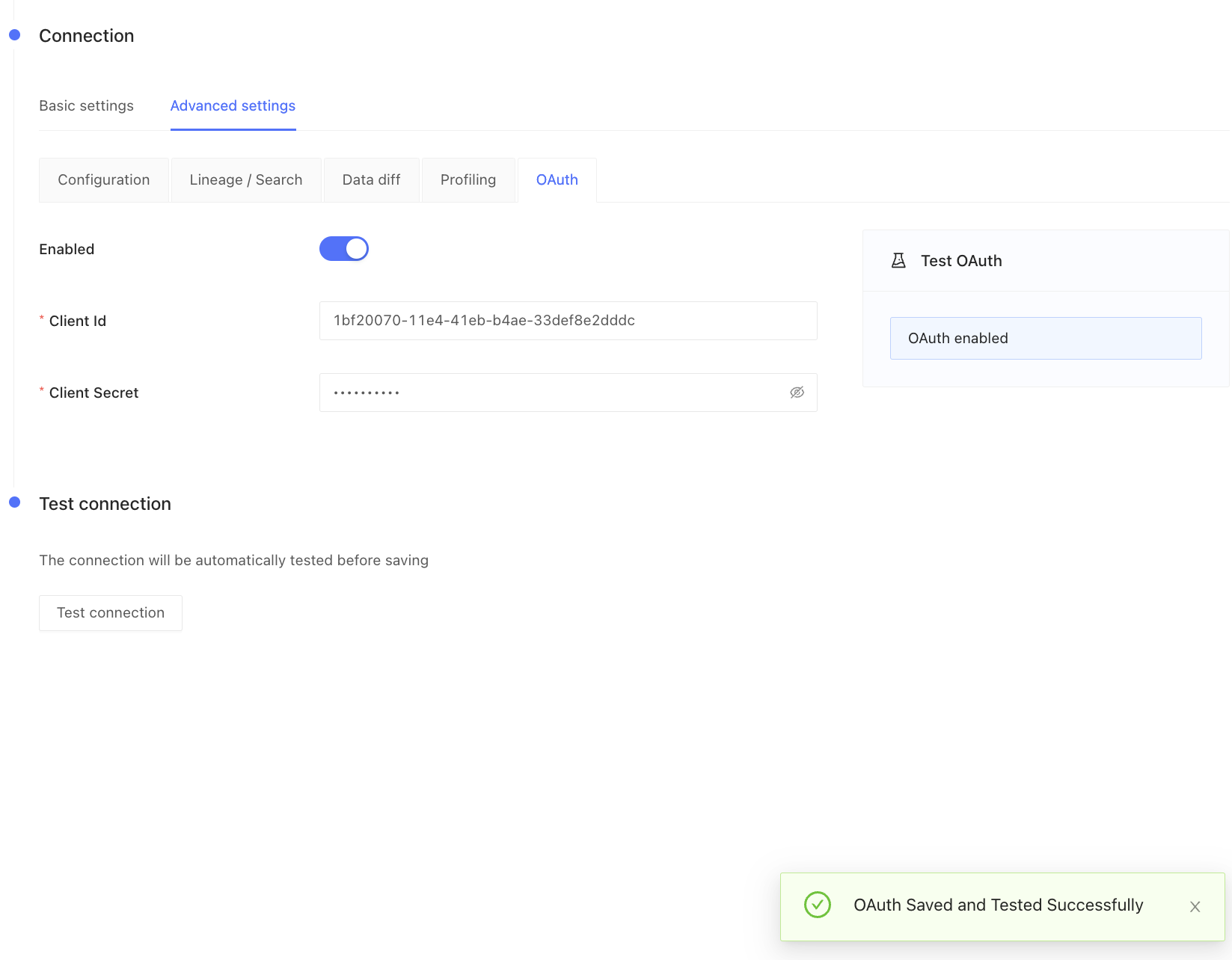
- Fill in the Client ID and Client Secret fields in Datafold’s Data Connection advanced settings:
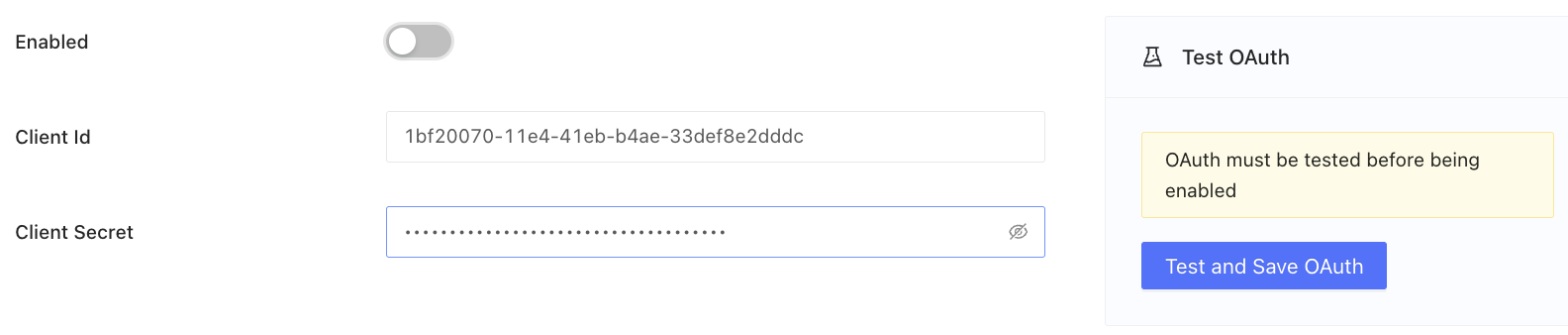
- Click Test and save OAuth. You will be redirected to Databricks to complete authentication. If you are already authenticated, you will be redirected back. This notification signals a successful OAuth configuration:
Additional steps for Databricks
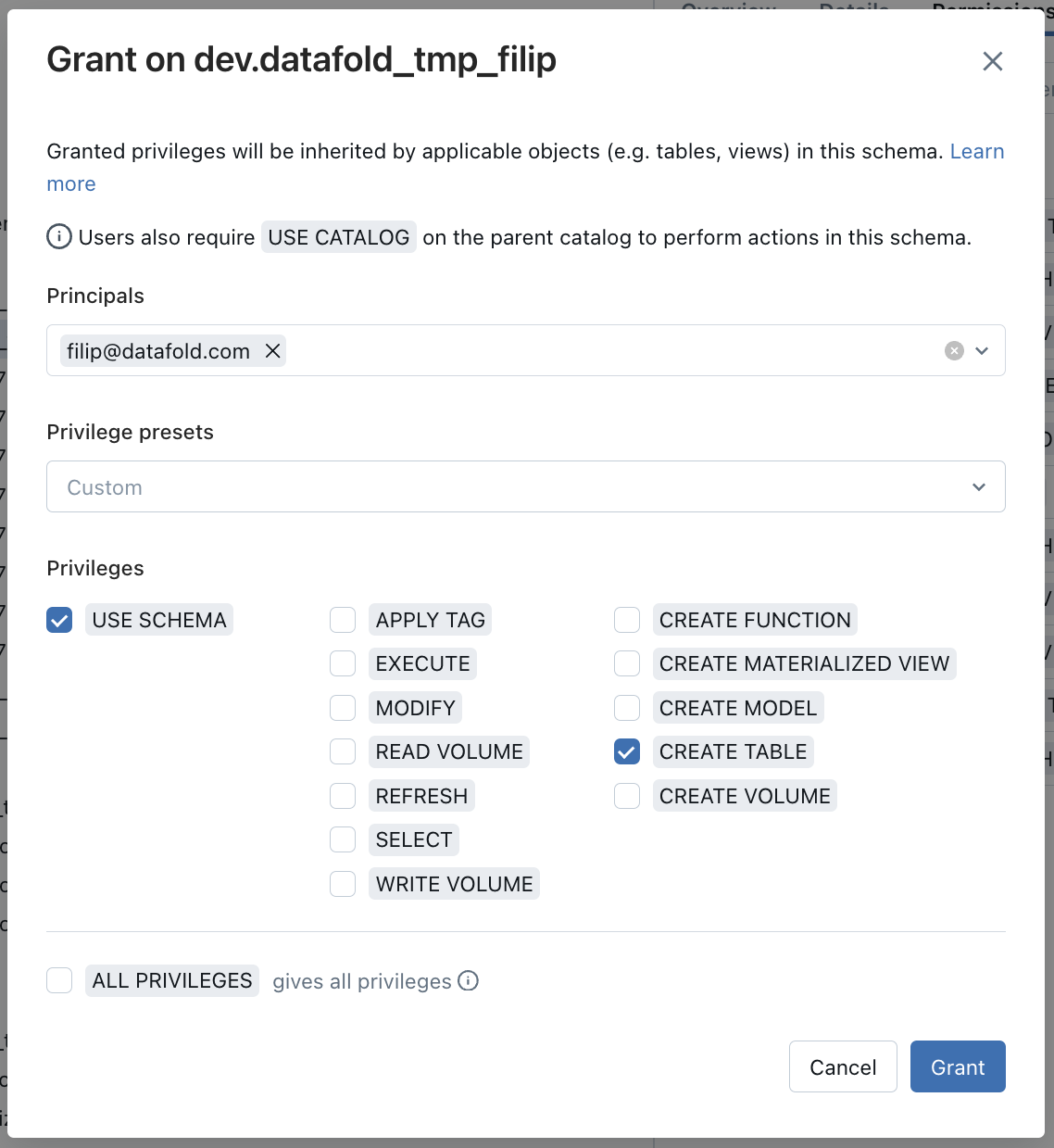
To ensure that users have correct access rights to temporary tables (stored in Dataset for temporary tables provided in the Basic settings for the Databricks connection), follow these steps:- Update the permissions for the Dataset for temporary tables in Databricks.
- Grant these permissions to Datafold users: USE SCHEMA and CREATE TABLE.
Example: Snowflake
To create a new Snowflake app connection:- Go to Snowflake and run this SQL:
Datafold caches access tokens and uses refresh tokens to fetch new valid tokens in order to complete the diffs and reduce the number of times users need to authenticate against the data warehouses.
OAUTH_REFRESH_TOKEN_VALIDITY can be in the range of 3600 (1 hour) to 7776000 (90 days).- To retrieve
OAUTH_CLIENT_IDandOAUTH_CLIENT_SECRET, run the following SQL:
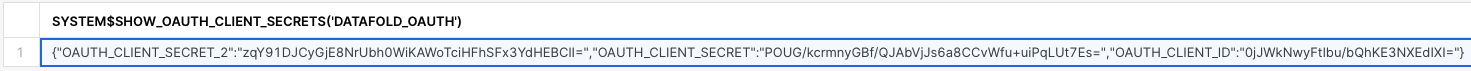
- Fill in the Client ID and Client Secret fields in Datafold’s Data Connection advanced settings:

- Click Test and save OAuth. You will be redirected to Snowflake to complete authentication.
Your default Snowflake role will be used for the generated access token.

Additional steps for Snowflake
To guarantee correct access rights to temporary tables (stored in Schema for temporary tables provided in the Basic settings for Snowflake connection):- Grant the required privileges on the database and
TEMPschema for all roles that will be using the OAuth flow.
- Revoke
SELECTprivileges for tables in theTEMPschema for all roles that will be using the OAuth flow (except for theDATAFOLDROLErole), if they were provided. This action must be performed for all roles utilizing the OAuth flow.
Example: Redshift
Redshift does not support OAuth2. To execute data diffs on behalf of a specific user, that user needs to provide their own credentials to Redshift.- Configure permissions on the Redshift side. Grant the necessary access rights to temporary tables (stored in the Schema for temporary tables provided in the Basic settings for Redshift connection):
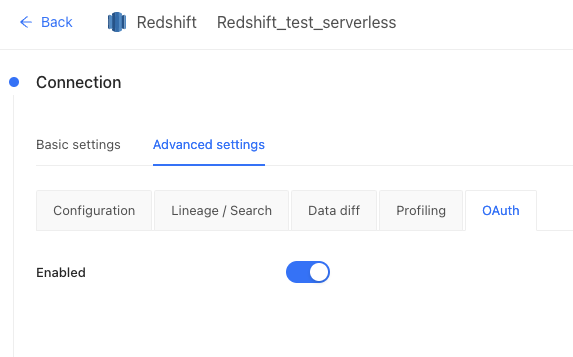
- As an Administrator, select the Enabled toggle in Datafold’s Redshift Data Connection Advanced settings:
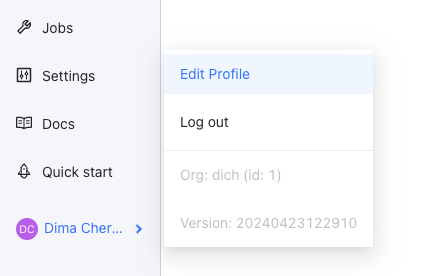
- As a User, add your Redshift credentials into Datafold. Click on your Datafold username to Edit Profile:
Example: BigQuery
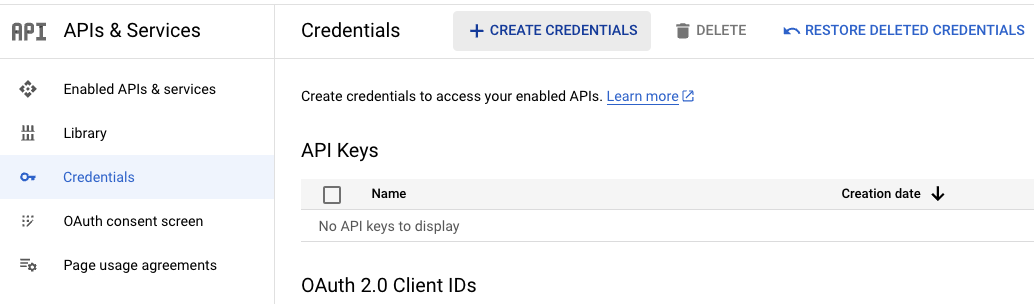
- Create a new Google Cloud OAuth 2.0 Client ID. Go to the Google Cloud console, navigate to APIs & Services, then Credentials, and click + CREATE CREDENTIALS:
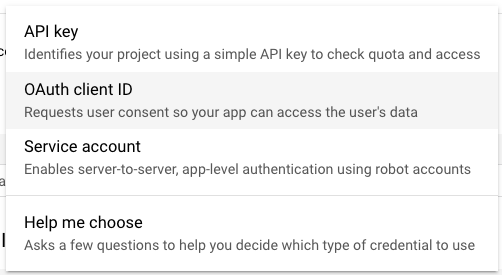
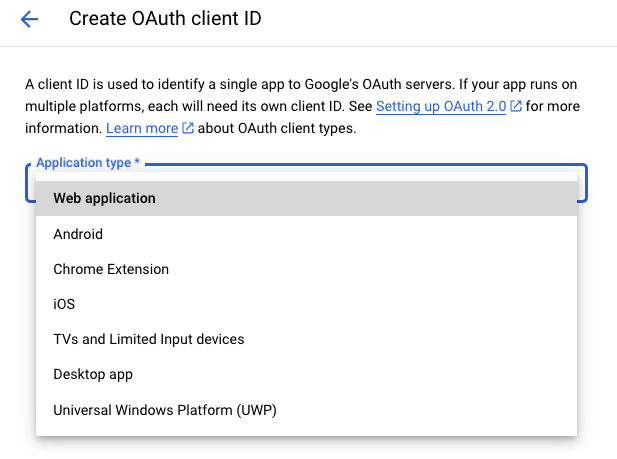
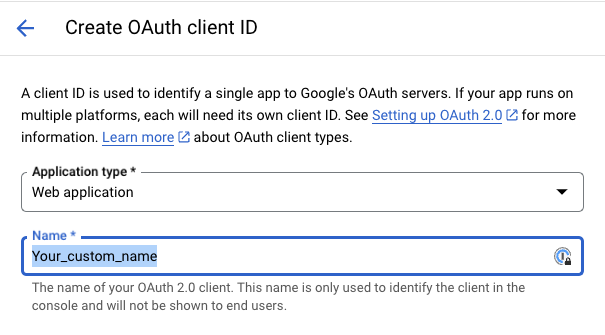
https://app.datafold.com/api/internal/oauth_dwh/callback:
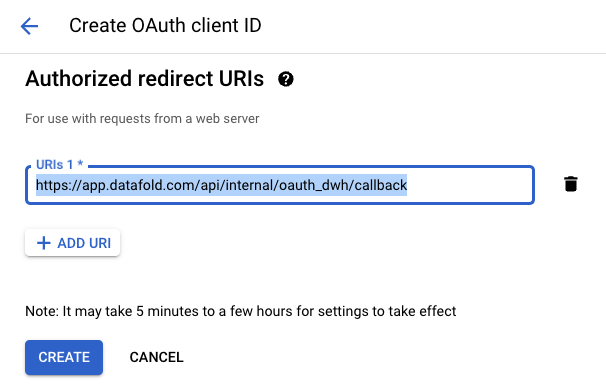
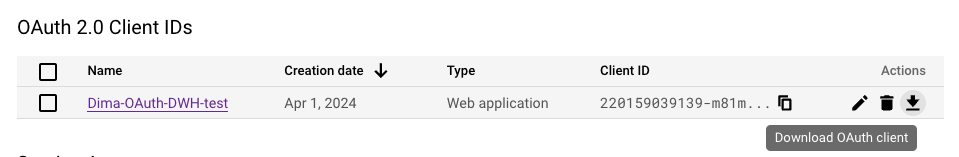
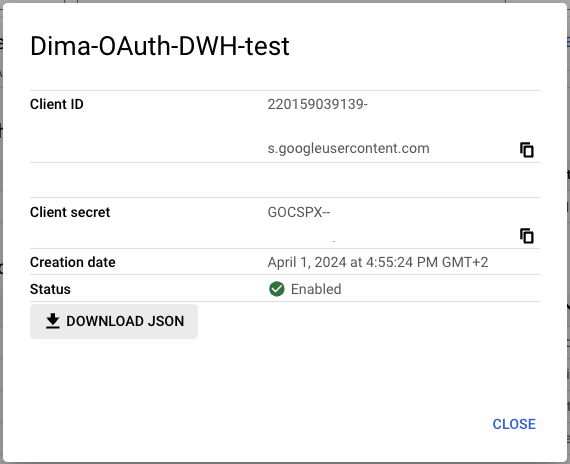
- Activate BigQuery OAuth in Datafold by uploading the JSON OAuth credentials in the JSON OAuth keys file section, in Datafold’s BigQuery Data Connection Advanced settings:
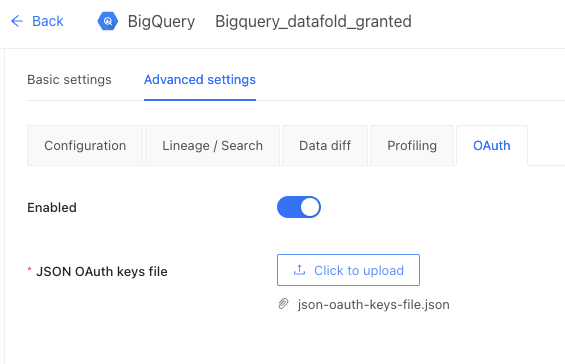
Additional steps for BigQuery
- Create a new temporary schema (dataset) for each OAuth user.
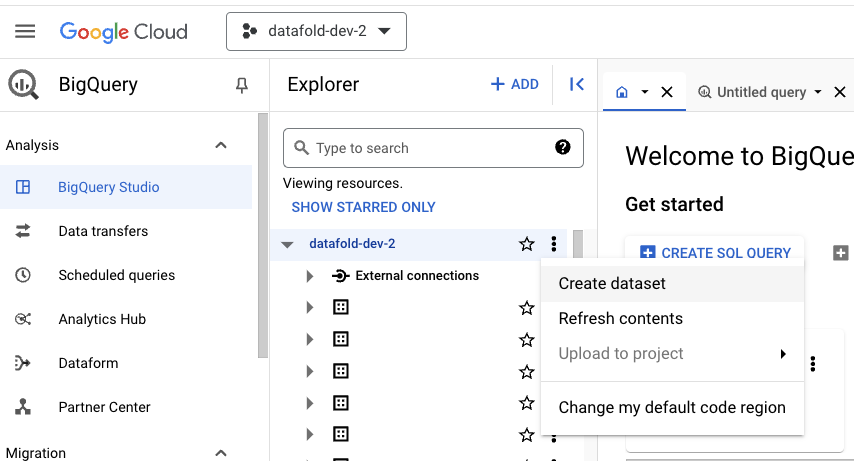
datafold_tmp_<username> as the Dataset ID and set the same region as configured for other datasets. Click CREATE DATASET:
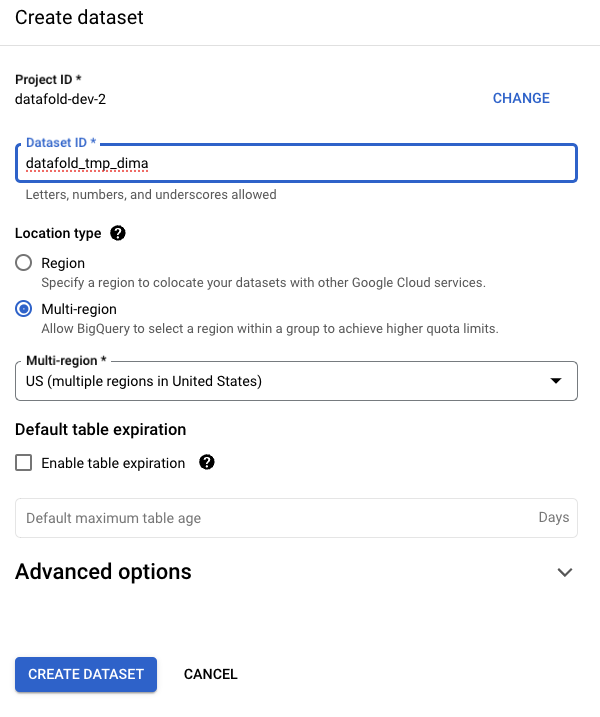
- Configure permissions for
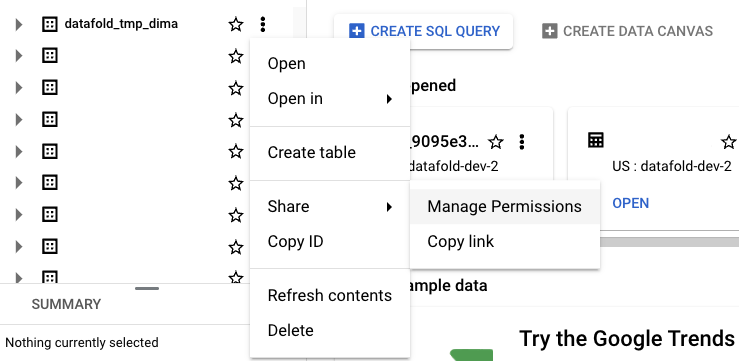
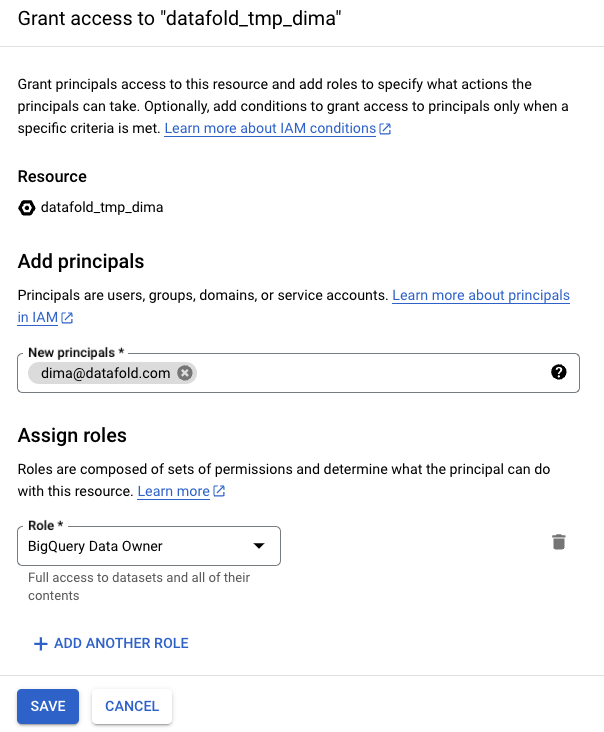
datafold_tmp_<username>.
datafold_tmp_<username> schema. This can be done by granting roles like BigQuery Data Editor or BigQuery Data Owner or any custom roles with the required permissions.
Go to Google Cloud console, navigate to BigQuery, select datafold_tmp_<username> dataset, and click Manage Permissions:
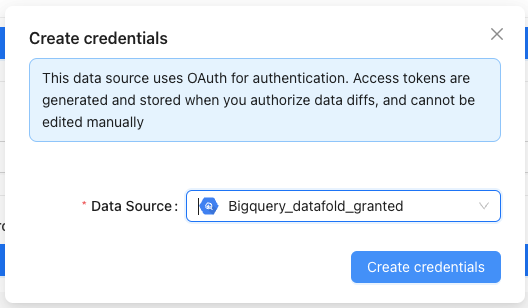
- Configure temporary schema in Datafold.
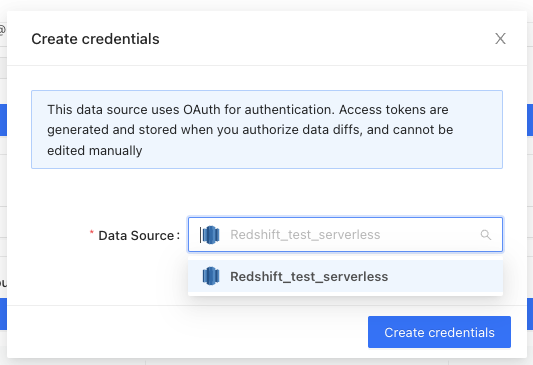
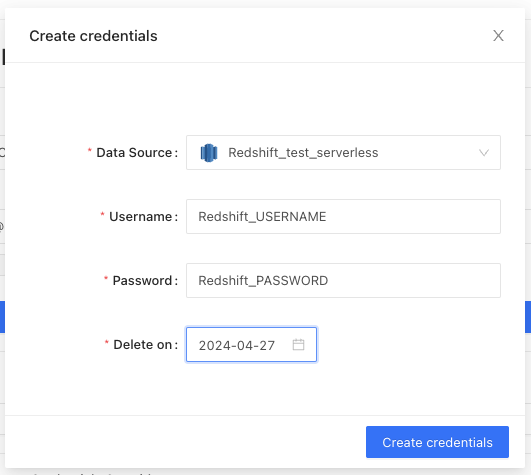
https://app.datafold.com/users/me. If the user lacks credentials for BigQuery, click on + Add credentials, select BigQuery datasource from the list, and click Create credentials:
accounts.google.com and then returned to the previous page:
<project>.<datafold_tmp_<username>>, and click Update:
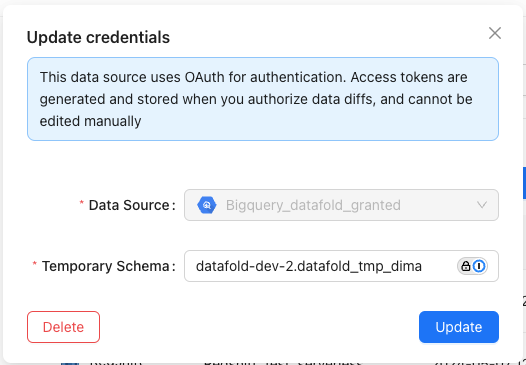
Users can update BigQuery credentials only if they have the correct permissions for
<datafold_tmp_<username>.